First of all, you must ensure that each side has its own key as well as the public key or the certificate of the other. It is recommended to create a separate key for VPNs on each system.
If you set up multiple VPNs on the Intra2net system, you do not have to create a separate key for each connection: you can use a separate key for all VPNs. Of course, only the public key is required from each of the peers.
It is therefore best to create a certificate for VPNs as described in Section 45.2.1, „Create certificate“.
Further details on key management can be found in 44. Chapter, „Key Management“.
A connection configured on the Intra2net system applies to the connection between a client and a network behind the Intra2net system. If you want to access multiple networks behind the Intra2net system from the one client, multiple connections can be easily configured. Make sure that you always use the same combination of keys and certificates for each of these connections.
You can configure VPN connections in the Services > VPN > Connections menu.
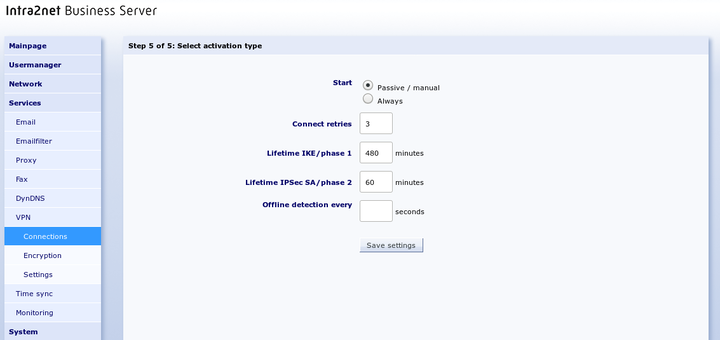
To manually configure a new connection, select "".
Set the options for the peer. The peer is not usually known on individual clients. Therefore, set it to "Dynamic IP (Road Warrior)".
The encryption algorithms used can be selected using the encryption profile; for details see Section 43.5, „Algorithms“. It is important that the settings for Perfect Forward Secrecy (PSF) are identical on both sides.
Encapsulation controls how the packets for the VPN tunnel are packed. With ESP, encryption and authentication are encapsulated. ESP+AH uses separate encryption and authentication. ESP+AH cannot be routed through NAT, so it is strongly recommended to use ESP for individual clients. This setting must be identical on both sides of the connection.
Select your own key and the key of the remote side.
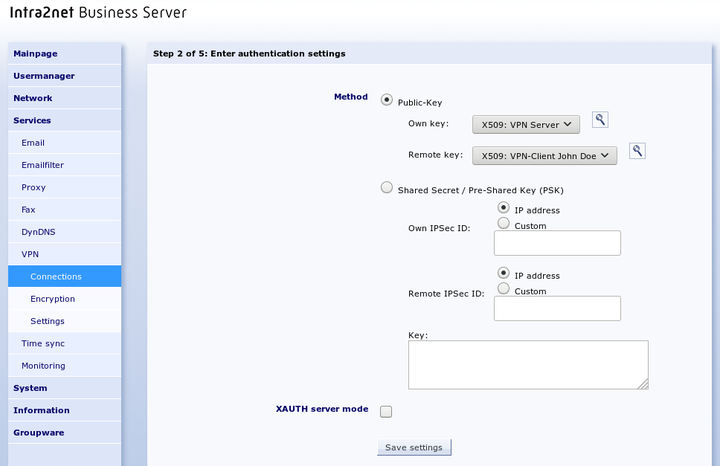
Some client programs offer the option of verifying a user's login and password in addition to authentication using a pre-shared key (PSK) or certificates. This is done using the Extended Authentication (XAUTH) protocol. If this is to be used by clients, activate the option "".
The XAUTH server mode now prompts the client from this connection to log on with the credentials of a user who has the group right "" on the Intra2net system. You can assign this group privilege on the "" page.
For the reasons mentioned in Section 43.6, „Limitations“ we advise against authenticating connections using a pre-shared key (PSK). This solution is particularly dangerous for multiple portable devices.
On the "Tunnel" page, you can configure which network is connected to which virtual client IP via this VPN connection.
The "" option selects the network to be connected on the Intra2net system side. With the option "" select one of the networks directly connected or routed to the Intra2net system.
If you want all client traffic to run through the Intra2net system and thus also benefit from the firewall and proxy server, select the "" option for "".
For "", select "". Select a previously unused IP that is not located on one of the networks of the Intra2net system or client. This is the virtual IP that you must also enter into the client. Always use 255.255.255.255 as the netmask.
Most VPN clients can have their virtual IP and related DNS servers automatically assigned via the Mode Config protocol extension. If your client supports this (e.g. Shrew Soft, NCP or iPhone, see the description of the individual clients), set the "" option to "" and enter the IP that the client should get. As a DNS server, the Intra2net system automatically transmits its own IP.
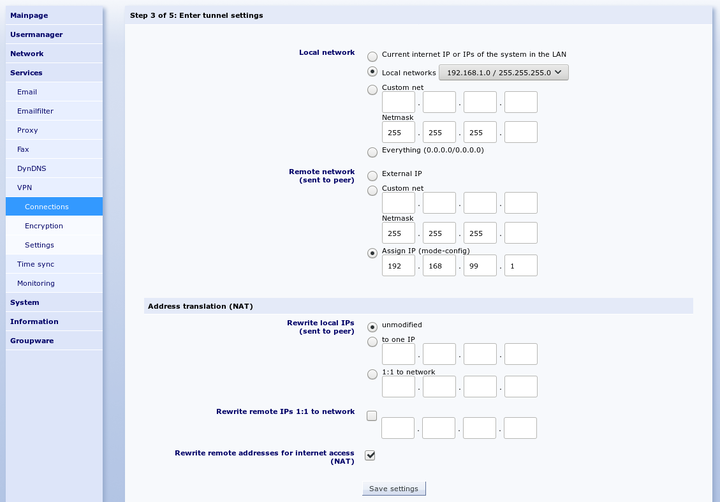
If "" has been set to a network containing addresses that are not located in local or other VPN networks, the client can access the Internet via the VPN. This applies in particular to the setting "". Since the virtual IP usually originates from a private address range, it can be rewritten to the external address of the Intra2net system (NAT) via the "" option. This NAT is only active when accessing the Internet, accesses to the local network continue to be made with the virtual IP.
Further options for address conversion (NAT) are explained in 57. Chapter, „Solving IP Address Conflicts in VPNs Through NAT“.
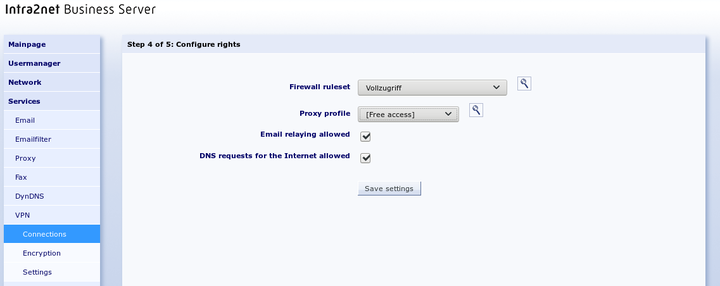
This menu defines the rights of the VPN client. This applies to all packets coming from the VPN client. A description of the rights options can be found under Section 8.3, „Access Rights of a Network Object“.