Table of Contents
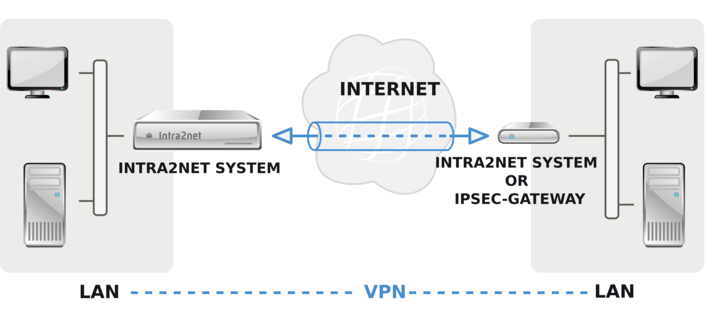
If multiple clients on a remote network are to be connected to a network behind the Intra2net system (e.g. in a branch office), it is generally more practical to establish a VPN between the two networks instead of setting up a single VPN for each of the clients.
The VPN is then established between the Intra2net system and an IPSec gateway ahead of the other network. This IPSec gateway can be an Intra2net system, but it can also be another compatible product.
Networks can also be connected to private IPs via a VPN tunnel. However, the IPs continue to be used for addressing. This means that you cannot connect networks with identical or overlapping network areas via VPN.
Make sure that the Intra2net system and the IPSec gateway on the remote station get an official IP and are not behind a router that uses NAT. Although VPN behind a NAT router is possible, it can cause difficulties if both sides are behind NAT routers.
It is not necessary to use dedicated IPs. Dynamic IPs with DynDNS can be used on one or both sides without difficulty.
If the connection on one side is disconnected regularly (e.g. by forcibly disconnecting DSL), it should be ensured that the connection can be re-established from both sides and not only from one.
A connection configured on the Intra2net system is valid for the connection from a network on the side of the peer and a network behind the Intra2net system. If you want to connect multiple networks, you can configure a separate connection for each network combination. Make sure that you always use the same combination of keys and certificates for each of these connections.