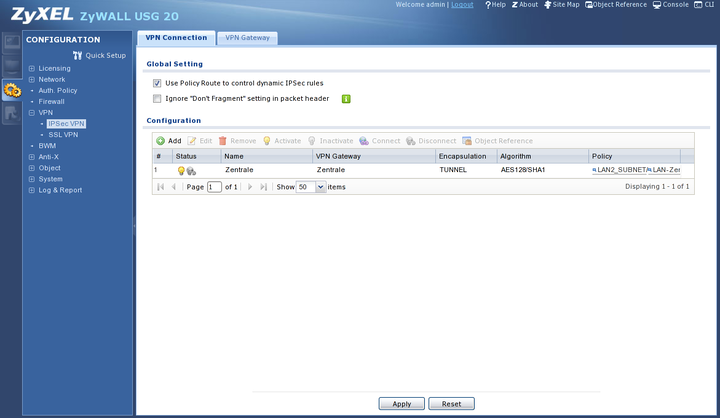
Open "" VPN Gateway tab. Create a new IKE connection to a peer with "".
Click "" to see all of the necessary fields.
Enter the IP or DNS name of the Intra2net system as the peer gateway address. Even if the Intra2net system uses a dynamic IP with DynDNS, you must select "".
Specify the authentication on certificates and select the previously created certificate for the ZyWALL.
Select AES128 and SHA1 as Proposal, the matching "" is DH2.
If the Zywall or Intra2net system is located behind a NAT router, you need to enable "".
Go to "" VPN Connection tab. Create a new IPSec connection with "".
Create a network object for the network of the peer. Use the "" menu. Use
SUBNETas type and enter the network address and netmask.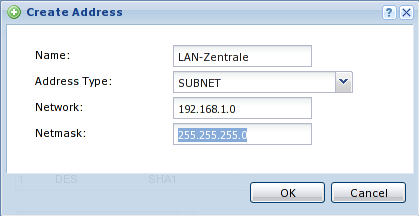
Click "" to see all of the necessary fields.
Set the connection to Nailed Up so that ZyWALL keeps the connection open automatically.
Select Site-to-site and select the newly created IKE connection to the Intra2net system as gateway.
Select the network to be connected behind the Zywall as "". As "" select the network object you just created with the network of the Intra2net system.
Activate "" to ensure that the connection is secure against network manipulation.
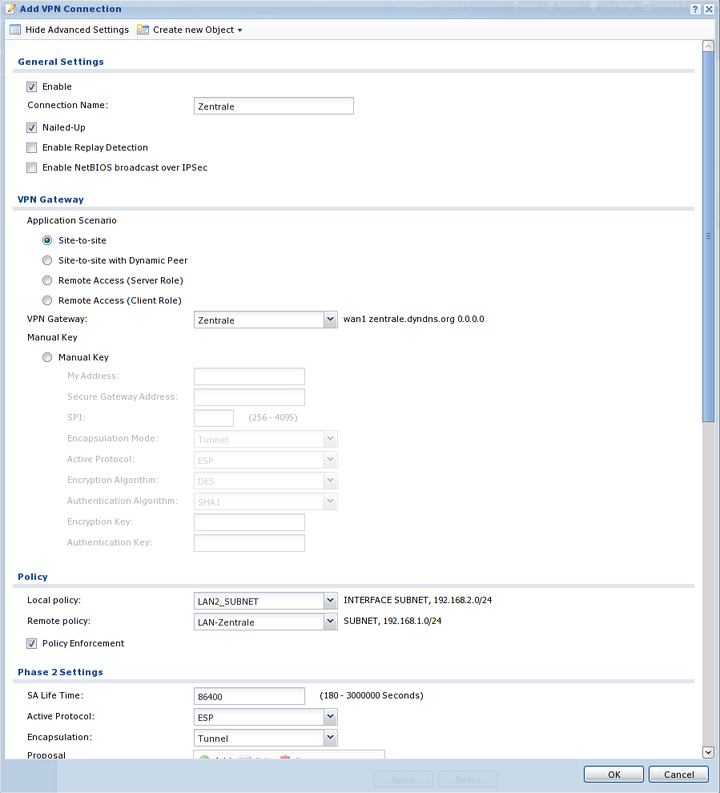
Select "" AES128 and SHA1, set "" to DH2.
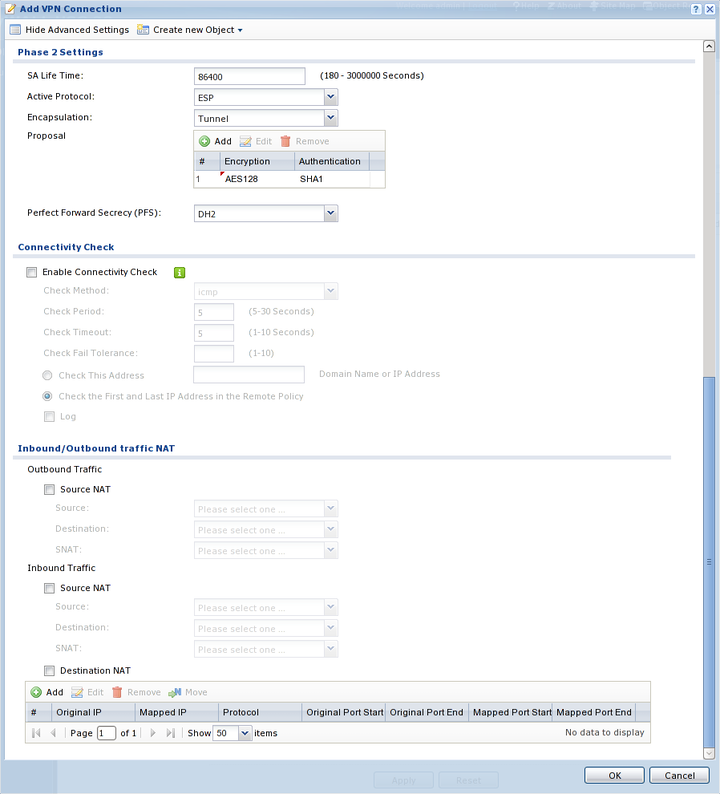
The connection is now configured and should be established in the background.