The Lancom router requires a special configuration of the Intra2net system certificate. Since version 8 of the LCOS firmware, self-signed keys have not been accepted, only certificates signed by an independent CA. The following shows how such a key can be generated and signed on the Intra2net system.
Firstly, the certificate must be created for the CA: In the Intra2net system, open System > Keys > Own Keys : Data. Click on the menu item "New" to start key creation. The certificate is only used to sign the actual encryption certificates, so we call it
server-ca(to be entered in the "" and "" fields).This CA certificate must now be given to the Lancom router. To do this, export it from the Intra2net system using the "" option. Then in LANconfig, open the context menu "" of the relevant device. Select the option "Upload certificate or file".
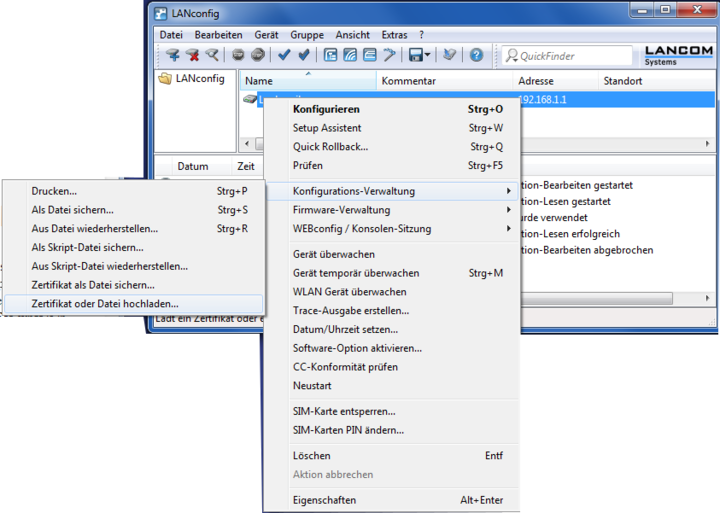
Select the
.pemfile just created and upload it as the certificate type "".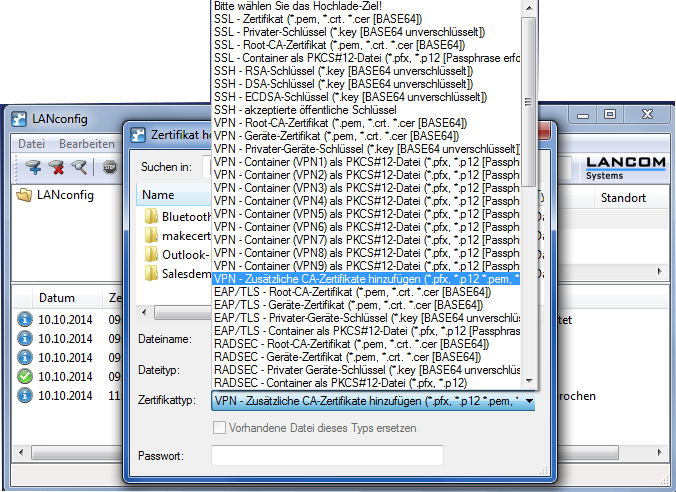
Now return to the Intra2net system under System > Keys > Own Keys : Data. Create another key as the foundation for the VPN certificate. Please note that the value in the "" field (i.e. the "Common Name" of an SSL certificate) is later entered into the Lancom router exactly, without tolerance for deviations. Therefore, make sure that you do not make any typos at this point!
Now go to the System > Keys > Own Keys : CA menu on the Intra2net system and select the recently created VPN key. In the "" section , select the CA key created in the previous steps (
server-ca) and then click "".Now check the value "" under System > Keys > Own Keys : Data. The data specified when the CA certificate was created should be summarized in this field. (If you follow the above example, this field contains the string
CN=server-ca. The key can now be used to establish a VPN connection.