If you receive your emails directly via SMTP, as a first step in spam filtering, you can have emails from known spam addresses rejected immediately before they are accepted. This reduces the load on the system and avoids unnecessary data transfer.
If the "" option in the menu under Services > Emailfilter > Spam > Settings is active, the IP of each server that wants to deliver emails directly via SMTP is checked using DNS. Multiple block lists are queried. If the IP is listed on multiple block lists at the same time as a spam sender, the email is rejected by the server.
If the IP of the sending server is only present on a few or no block lists, the email is accepted and checked by the next level of the spam filter.
The Intra2net system contains a multi-level spam filter. An email is categorized both by spam-typical criteria (special words, many exclamation marks, invalid sender addresses, etc.) and by a bayesian word filter. The bayesian word filter can calculate spam probability by comparing word combinations with a pre-trained word base.
In addition, DNS-based network tests can be performed. It checks whether the email addresses and URLs contained in the email appear in different blacklists. Since this check is also performed for each internal email, you should only activate this option if your Internet connection is not charged by time or dial-up attempt.
Additionally, the Intra2net system can also check emails using the Razor network. The Razor Network is an association of email recipients. In the Razor network, spam emails are manually marked as spam. This information is then distributed via the Razor network. The more people classify an email as spam, the faster it is filtered out.
If the spam filter is activated (under Services > Emailfilter > Spam > Settings), a spam score is determined for each email and stored in a special email header. However, this does not delete or move an email. The score is stored in the header "X-Spam-Level:". It is calculated by (spam points+100)*10, which means that the value is always positive and an integer, which makes it possible to compare it in most other programs. In addition, a detailed description of why an email is spam or not is stored in the "X-Spam-Status:" header.
The higher the spam score, the more likely it is to be spam. Values lower than 4 are typically indicative of non-spam emails. With values between 5 and 8, the probability of spam is higher, but there is still a risk of it being a desirable email. With values of 8 and higher, the email is extremely likely to be spam.
The lower the threshold, the more emails are filtered out. At the same time, however, there is a greater risk that an important email will be sent to the spam folder.
In the Intra2net system, a distinction is typically made between three categories: desired email, potential spam and spam.
The potential spam is intended for emails that have clear spam characteristics but cannot be clearly classified as spam. It is advisable to check these emails regularly (e.g. weekly) manually.
Spam is an email that has been definitely identified as spam. These emails do not normally need to be checked manually. However, in the event of erroneous configurations it is still advisable not to delete these emails immediately but to keep them for a few days.
As a reasonable compromise, the thresholds 5 for potential spam and 8 for spam have proven to be appropriate for most cases.
Under Services > Emailfilter > Spam > Global the global spam filter can be activated. It filters all received emails - regardless whether they go to a local user or get forwarded. Therefore, we recommend the Global Spam Filter especially in cases where emails are not permanently stored on the Intra2net system but forwarded to another server.
The following filter actions can be configured separately for spam and potential spam. This allows the two categories to be treated differently.
The "" option ensures that each affected email is preceded by "***SPAM***" or "***POTENTIAL SPAM***" in the subject line. This makes sense especially when emails are delivered normally.
With "" the concerned emails continue their normal process and are not stopped or redirected. This is particularly useful in combination with changing the subject and a filter rule on the target server. The filter rule on the target server can then store the emails in an appropriate subfolder based on the subject.
The "" option redirects the affected emails to a group address. If you are using an account on the Intra2net system, please make sure to activate the user-dependent spam filter and have the spam emails deleted automatically after some time. Otherwise, there is a risk that the spam account will grow indefinitely.
The spam quarantine stores detected spam emails, keeps them waiting for a specified time and then deletes them. If necessary, mis-identified emails can be released from quarantine and delivered normally.
The spam quarantine itself is available under Services > Emailfilter > Quarantine > Spam. It contains the detected spam emails of all recipients together. Therefore, it is normally only accessible to users with administrative rights. It can also be made accessible with a data protection password under Information > Data privacy, only using the 4-eye procedure.
The report function is available to give each recipient an overview of their filtered emails. When activated, each recipient will automatically receive an email with an overview of all filtered emails within the specified delivery times.
The report email contains a link under the data for each filtered email that can be used to release the relevant email from quarantine. The report emails are sorted by increasing likelihood of spam.
![[Hint]](../images/admon/note.png) | Hint |
|---|---|
Since the report emails contain the subject lines of the filtered emails, it is possible that an additional spam filter installed on the destination server or client may incorrectly identify the report emails as spam. If you use an additional spam filter it is recommended to enter the postmaster address of the Intra2net system (found under Services > Email > Settings) in your whitelist. The postmaster address of the Intra2net system is used for sending the reports. |
The user-dependent spam filter can be individually configured for each user on the Intra2net system. It is able to store detected spam emails in special IMAP subfolders belonging to the user. We therefore recommend using the user-dependent spam filter in cases where the emails are to be finally stored on the Intra2net system.
If an email reaches a user who has activated the spam filter under Usermanager > Users : Spamfilter, the email is scanned. The user spam filter has a two-stage structure. There is a threshold value for potential spam emails as well as a threshold value for "real" spam. If the email has a spam point value greater than or equal to the entered threshold value, it is not deleted but placed in the IMAP subfolder "Potential Spam" or "Spam" belonging to the user. If desired, spam emails can also be forwarded to a central collection address.
Additionally, every user has the option to influence this by using a blacklist (all senders or recipients listed are always classified as spam) and whitelists (all senders or recipients listed are never classified as spam).
When a user accesses their emails via IMAP, the subfolders are directly visible. It may be necessary to reload the folder list in the email program and subscribe to the folders (subscribe). Spam emails remain on the server when accessed via POP3. The user should therefore regularly check the "potential spam" folder for incorrectly filtered messages via webmail.
In standard mode, the spam filter checks all received email headers to see if their IPs are included in DNS blacklists. In optimized mode, only the IP of the sender's last server is checked. This further increases the spam detection rate and reduces the potential for false positives. The currently used mode can be found under "".
In order to distinguish the IP of the last sending server from falsified data, the system needs to know which servers are trustworthy. An SMTP server is considered trusted if it can be assumed that it does not distort the received lines in the email header and truthfully inserts its own received record. One can normally assume that all servers configured for receiving and processing their own emails are trusthworthy, since their operators are bound by contract.
The Intra2net system automatically tries to determine the trusted servers, using an adapted procedure for each email receiving method.
Trusted servers for direct SMTP and POP multidrop accounts. The Intra2net system automatically queries the servers responsible for receiving emails (MX record of the domain) for each configured domain via DNS. These servers are added to the list of trusted servers.
In the following cases, it may be necessary to adjust the list of Trusted Servers:
The emails are accepted by the server responsible for receiving the emails (MX record of the domain) and then forwarded to another server (e.g. for checking or caching) before they are sent to the Intra2net system. Here, the IPs or DNS names of all intermediate servers must be entered in the list of "Additional trusted servers".
The Intra2net system gets to see other data for its own domain via DNS in the local network than "outside" on the Internet. This configuration is usually called "split DNS". Here, the IPs of all externally responsible servers (MX record of the domain) must be entered in the list of "Additional Trusted Servers".
The emails for domain A are received by a server, rewritten to domain B and then forwarded to the Intra2net system or a server responsible for domain B. The Intra2net system only knows domain B. Here the original domain A must be included in the list of "trusted domains".
Trusted Servers for individual POP accounts. The Intra2net system automatically checks all email servers entered under Services > Email > Polling via DNS. These servers are treated as trusted. In addition, each server name is shortened to the second level domain, e.g. the server name "pop.1and1.de" is translated to the domain "1und1.de". The email servers responsible for this domain (MX entries) are queried and additionally saved as trusted servers.
In the following cases it may be necessary to adjust the list of Trusted Servers:
The provider uses different servers for their own emails from those of their customers. In this case, enter the domains of all email addresses used by you in the list of "Trusted Domains".
The emails are received by the provider on one server, e.g. forwarded to another server for checking and then again held ready for collection on another server. In this case, you must enter the IPs or DNS names of all intermediate servers used for checking in the list of "Additional trusted servers".
Emails are received from one domain and automatically forwarded to another domain. The Intra2net system then retrieves the forwarded emails. In this case, enter all original domains that are being forwarded into the list of "trusted domains".
Based on the last 1,000 spam emails, the Intra2net system is able to detect whether the list of trusted servers is correct. After this calibration, the spam filter switches to the optimized mode if possible. The calibration is checked hourly during operation.
![[Hint]](../images/admon/note.png) | Hint |
|---|---|
After changing the trusted servers or domains, up to 1,000 spam messages are required before the spam filter automatically switches to the optimized mode. |
Under Services > Emailfilter > Antivirus you can activate the email virus scanner. If it is activated, all emails passing through the Intra2net system (incoming, outgoing, forwarded, etc.) are checked for viruses.
If a virus has been found, it is quarantined under Services > Emailfilter > Quarantine > Virus and can be inspected by an administrator.
If a virus is found, warnings can be sent to the administrator and the recipient. Warnings are only sent to local recipients.
The virus scanner features cloud-based virus detection. Checksums are generated by executable files and sent to a data center. If the checksums are known to be malicious, the email is blocked. This significantly reduces the time between the first appearance of a virus and its detection. For data protection reasons, the data center receives only checksums and file names, not complete files.
In addition to viruses and Trojans, the virus scanner can also detect adware and spyware. Should such a detected program have utility, then detection can be switched off.
The virus scanner contains a component for detecting macro viruses using heuristic analysis. The detection level for heuristics can be adjusted. At higher detection levels, more macros can be recognized as a virus, but this also could result in an increased proportion of files wrongly detected as a virus.
Email attachments may contain new, unknown viruses. These must be delivered to a computer as an executable files before they can cause damage. The Intra2net system can scan email attachments and block particular file types. This will ensure that no executable file can reach a computer on the intranet via email.
The attachment filter examines attachments based on the file extension and MIME type. Additionally, it performs a type identification on the data actually contained within the email. Archives such as ZIP or RAR, as well as PDF are unpacked and scanned.
Under Services > Emailfilter > Attachment > Filter Lists, you can create filter lists for attachments. There is a distinction between whitelists and blacklists. Whitelists only allow known and approved attachments to pass through, whereas blacklists allow everything other than the listed entries to pass through.
Encrypted archives (protected with a password) cannot be scanned by the attachment filter. In practice, there are often viruses that are sent in encrypted archives and whose password is contained in the text of the email or an attached image. Therefore, it is generally recommended to filter out encrypted archives.
Some companies handle a significant proportion of communication with encrypted PDF files. In this case, it is possible to define exceptions for encrypted PDFs. These only apply to certain sender addresses defined in the corresponding field. Since the sender address of emails can easily be falsified and it has been observed in practice that, f.e. on infected systems of business partners, the email programs are systematically harvested by the attackers for email addresses communicating with each other, it is not recommended to let encrypted attachments pass completely unfiltered.
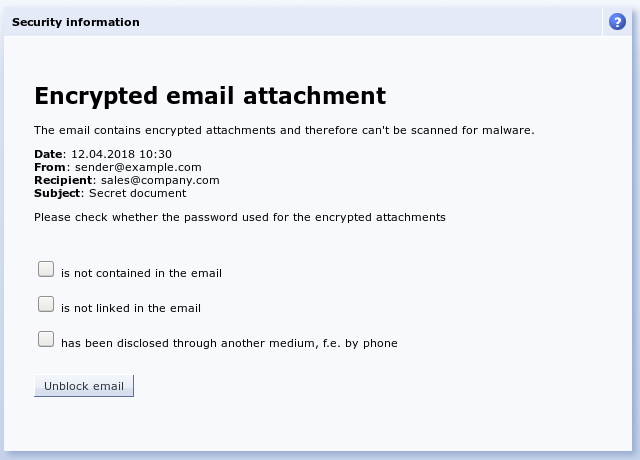
The recipient should always check emails with encrypted attachments to ensure that the used password is not contained or linked in the email itself, but has been previously established by the other communication partner using an alternative method such as telephone. To point out the necessity of this check to the receiver, it is possible to use "". Instead of the attachment, the recipient receives a link under which they must confirm the necessary checks and then release the attachment itself.
Because Office files can contain executable components (macros, VBA script, etc.), it is possible to scan Office files for such elements. By using the "" option, no specific Office file filtering is carried out, only the settings defined under "" will apply. By using the "" option, Office files are opened and any existing macros are extracted and analyzed. If an Office file contains macros that fulfill multiple common malware criteria, the file is blocked. With the "" option, all Office files that contain macros are automatically filtered.
There are predefined filter lists "All Permitted","All Forbidden" and "Executable Files". Under Services > Emailfilter > Attachment > Settings you can define global settings for the attachment filter and the "Default filter list". The default setting is "Executable files". Outgoing emails and domain forwarding are also filtered through this default list.
Incoming emails use the filter list of the user groups. This can be assigned under Usermanager > Groups : Rights. By default, all user groups use the default filter list. If one user is a member of multiple groups with different filter lists, the filter lists are merged. Whitelists have priority over blacklists. This, for example, makes it is possible to block all executable files, while still permitting them for the administrator group.
If an email is filtered, it is quarantined under Services > Emailfilter > Quarantine > Attachment and the administrator is notified. The email can easily be released or deleted later. Alternatively, it is possible for incoming emails to be delivered without the (potentially dangerous) attachment. The original email with attachment is still kept in quarantine and can be released if necessary.
Access to the quarantine can be allowed, as with any other menu item, under Usermanager > Groups : Administration rights for any user group, just like any other menu item.