If multiple official IPs are available and a server in a de-militarized zone (DMZ) is to be connected, this can be done in three different ways.
![[Hint]](../images/admon/note.png) | Hint |
|---|---|
Please note that at least 8 official IPs are needed in order to connect (at least) one server in a DMZ. |
| Advantages | easy to understand, widespread |
| Disadvantages | Wasted IP addresses due to network division, subnet routing must be specified on the router |
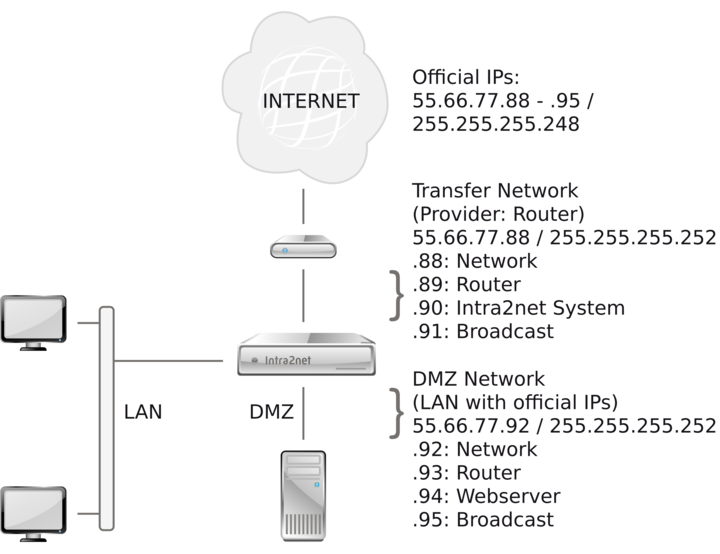
This variant divides the existing network with official IPs into two smaller subnets: A "transfer network" between router and Intra2net system and a DMZ network. Since each subnet always requires two IPs for network address and broadcast and the Intra2net system requires one IP on both networks, only one of the 8 official IPs is available for one server in the DMZ.
On the router it must be specified that the directly connected network (transfer network) has been reduced in size and that the DMZ network is routed via the Intra2net system. Since the user often has no access to a router supplied by the provider, this setting must be made by the provider.
| Advantages | flexible, good IP utilization |
| Disadvantages | does not work with all protocols |
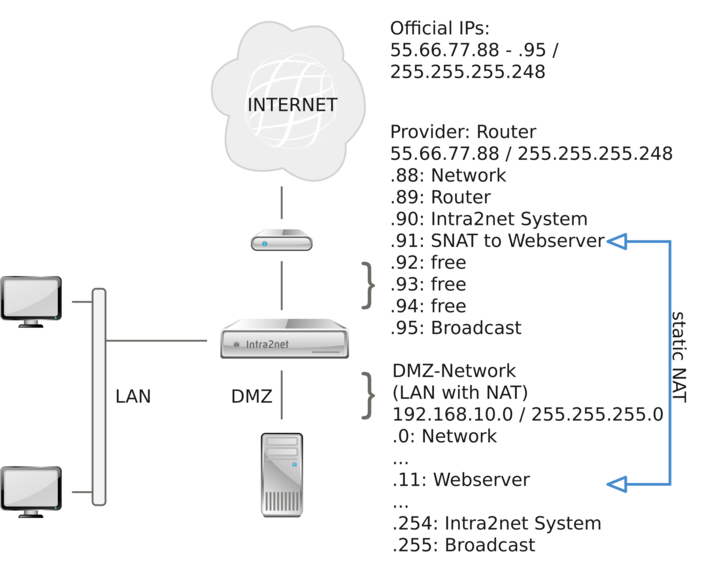
In this variant, the DMZ is set up like a normal LAN with IPs from the private address space (e.g. 192.168. x. x). Create all DMZ servers under Network > Intranet > Clients. Then forward the public IP to the server in the DMZ under Network > Firewall > Static NAT.
The Intra2net System automatically answers ARP-requests for the IPs with static NAT as soon as they are in the network between the router and the Intra2net System. Therefore it is not necessary to have any special routing entries on the router for these IPs.
Since the server only knows its IP from the LAN - but not its public one - some protocols do not work, because some protocols also transmit the IP used in the regular data stream. For some protocols, the Intra2net System can compensate for this (e.g. FTP and PPTP), but not for others (e.g. H. 323).
| Advantages | works with all protocols, good IP usage |
| Disadvantages | more complicated configuration |
With Proxy-ARP the network between router and Intra2net system is created again as a DMZ with the same data. Under Network > Interfaces select the type "Proxy-ARP" for the DMZ. Give the Intra2net system in the network the same IP as it was entered under Network > Provider > Profiles. Make sure that all clients in the DMZ network are entered individually under Network > Intranet > Clients. The Intra2net system assumes that all clients not registered there are located in the network between the Intra2net system and the router.
Set the default gateway on the server of the DMZ to the Intra2net system. The Intra2net system now mediates between the two divisions without the clients being affected in any way. For the clients it appears to be a single, larger network. The firewall controls the exchange of data between the two divisions.
It is not necessary to adjust any special settings for the internal network on the router.
![[Caution]](../images/admon/caution.png) | Caution |
|---|---|
Initial installation can result in problems with the router's ARP cache. The router will then think that the server is still in the network between router and Intra2net system. First configure the Intra2net system, then the DMZ server and then restart the router to avoid this problem. |
